Easy Passowrds to Type in With One Hand
This is the second part of our password series. In part 1, we talked about how passwords are cracked and what makes them easier or more difficult to crack depending on the type of attack, information an attacker has about you, etc.
If you're familiar with the power of two notations, entropy, sample space, and uniform randomness, I think you'll understand most of what I'll talk about below... if not, I highly recommend you go read the first part of this article before you read this one.
Before I present you what I think are good solutions to the password problem, let's talk about what are "bad passwords" first. One, so it's fresh on your mind while you read and think of ways to avoid them, and two, because I think you'll appreciate the suggestions more if you know what problems they solve.
The goal is that, by the end of this article, you will have all the necessary tools to create an uncrackable password. (While nothing is 100% secure, what lies ahead is the gold-standard when it comes to password creation today and should last for a very long time.)
What Pitfalls to Avoid When Creating Passwords
Is there such thing as a password too strong? We can answer that question in two ways: a practical one and a mathematical one. The mathematical is out of the scope of this article, so we'll look at it from a practical point of view today.
Consider, for instance, a password with 250 bits of entropy. Despite how big that entropy is and how secure it may look like, a password that strong would need some 40 (the minimum possible N when using all 95 valid characters so that 95^N is equal or greater than 2^250) randomized alphanumeric characters, and that makes it a horrible password for regular users.
"Avoiding password pitfalls is all about identifying unintended risks or consequences that can arise with the password you choose, despite it being a strong password."

Tweet This
The example above would be so cumbersome to use that dialing down its strength to "secure enough" would make it a better password.
There's a sweet spot to a good password — that depends on your personal preference, and we'll also talk about that — and finding that spot is what this article is all about. Below we're going to go over a few of those elements that are important to fine-tune when creating a password.
Security theater
When people realize they have poor passwords, they tend to have one of two possible reactions, in my experience:
- Continue choosing poor passwords. Not by choice, but because they don't actually understand how passwords are exploited. They even change the password, but it's equally bad as the one they had originally;
- Go to the other extreme and create prohibitively difficult passwords when they don't need to.
Option #2 is a good example of security theater: choosing an over-the-top one when a shorter would suffice – tactics that do little or nothing to increase your security yet feel like they do. Past a certain point, there's little to no gain in increasing length, even more, when the adversary would use easier alternatives to attack the user.
This is something that hits close to home because it's something I was guilty of.
Years ago, I decided to use an alphanumeric password instead of a numeric passcode on my phone. Not only that — at the time, I was not as well-versed in the arts of password-making — I thought that password length was the most important thing to keep in mind and opted for a 30-character password.
As you can imagine, it was extremely annoying to have to type a password that long, make a typo, and have to do it all over again, often multiple times. So annoying that I decided to change the password to something way easier to type by repeating a few characters multiple times until it added up to the (completely arbitrary) length of 30 characters.
That "helped" for a while but still was too much of a hassle, and over time I found myself unconsciously leaving the phone unlocked for longer so I wouldn't have to type the password every time I wanted to check something. Sometimes I'd even get up and leave it unlocked on my desk before realizing much later what I had done.
Eventually, I realized that trying to use a 200-bit password made it, paradoxically, less secure than, say, a 100-bit one (we'll talk about ideal strength in a moment).
Not only I was walking around believing my phone was secure because I had this huge password (despite it being one that I created myself, and probably susceptible to the biases we talked about in the previous article), but my attack surface increased as it made me more likely to take risks I normally wouldn't out of annoyance.
There are mechanisms put in place on iPhones that makes brute-force attacks harder to pull off so that you don't need to go to the same lengths to protect it as you would if you were worried about remote attacks:
- The perpetrator would have to get physical access (instead of a database dump from the Internet) to your phone in a one-hour window since you last unlocked it (this is a security feature Apple implemented to prevent brute-force attacks);
- Apple entangles the cryptographic key with the device UID multiple times using the PBKDF2 algorithm. The number of iterations is calibrated so that one brute-force attempt takes a lot of time (approximately 80 milliseconds);
- You can set up your iPhone to wipe out everything after ten failed attempts (that's why having a working backup is a crucial part of any security strategy).
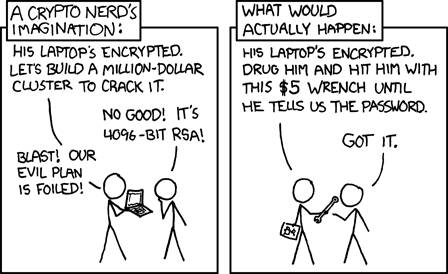
Credit: xkcd.
After reaching a good-enough point for your password, you'd be better off addressing other ways an attacker might be able to exploit your passwords.
Usability
As illustrated before, you have to consider where that password is going to be used.
Are you going to use it on your phone, where you'll tend to type with one hand while fumbling your coffee with the other, or are you only going to type it on your full-sized keyboard at home? Do you use your phone frequently, or just once or twice per day?
Another thing you have to consider is your preference when it comes to length or complexity. Do you prefer longer but simpler to type passwords or shorter but more-complicated-to-type ones? Both options can be equally secure, but one will appeal more or less to different folks.
Even if you use both hands, it can be quite complicated to type symbols on small touch keyboards — you have to press Shift multiple times, and in many instances, it takes much more time to type two or three symbols than one entire English word.
The more usable a password is, the more likely you are to keep using it. You want to increase its usability as much as possible. Note that this doesn't mean you should reuse passwords across different applications (use a password manager instead), but that you should make deliberate decisions to decrease the likelihood of you giving up before your new password becomes second nature.
There is a quote circulating among Security Stack Exchange circles that encapsulate this very well. It's known as "AviD's Rule of Usability":
"Security at the expense of usability comes at the expense of security."

Tweet This
Easiness to remember
A great password has to be easy to remember. An easy-to-remember password will give you confidence that you can memorize it eventually and will avoid situations where someone needs you to unlock your accounts on the spot.
Note that whether passwords like sBt$] [p'_3d {+@:(b-i(-y> H'x&'a) K are easy to remember or not depends on the person — I've met people who had zero problems creating mnemonics to memorize passwords like that, and I've met people that aren't too keen on them.
If that's hard for you, consider using passphrases: a list of real words strung together, such as swell posing gruffly slander onto. We'll talk about a method for creating passphrases like this further down below.
How to Create Great Passwords
With the pitfalls out of the way, let's talk about how to create great passwords.
A great password is one that has sufficient entropy, is resistant to dictionary attacks, and avoids all the previously mentioned pitfalls. The first thing we need to determine is what is sufficient entropy so we can determine the minimum length to avoid brute force attacks.
How long should it be?
Even though using entropy to measure password strength has some drawbacks, as we've talked about in the first installment of this series — if you can guarantee the password was generated uniformly and randomly — entropy is very useful because it gives you a number that we can compare against different benchmarks; we can quickly determine if a particular password is "out of reach" or not.
For example, the NIST, which is responsible for providing scientific standards in the US, used to recommend 80-bit passwords for cryptographic secrets (government documents, etc.) and updated that to 112 bits in 2014.
For comparison, the French equivalent to the NSA, ANSSI, rates passwords up to 64 bits as "very weak," between 64 and 80 bits as "weak," between 80 and 100 as "moderately strong," and above 100 as "strong." They require a minimum of 100 bits when it comes to passwords or secret keys for encryption systems that must be secure.
So, if you're using all 95 characters (lowercase and uppercase letters, numbers, and symbols), the minimum length your password must have to have an entropy of 80 bits is 13 characters.
But we also need to be able to resist dictionary attacks. The password Passw0rd1234! has 13 characters and a theoretical entropy of 85 bits, but it's a horrible password because it's a permutation of a known word (and also a widely used password).
To avoid dictionary attacks, you need to use words that aren't real, i.e., a string of gibberish created by a cryptographic generator or passphrases.
An Alternative: Diceware Passphrases
Diceware passphrases consist of a list of words that you can create randomly by throwing a fair dice five times, then comparing the result with a word list to come up with real words.
The list is provided on the official Diceware website and has 7,776 words in total, all possible permutations of five dice throws. The resulting passphrase will be something like rewrite Celtic life raft armed.
For example, say you roll a dice five times, and the results are six, one, four, six, and one. If you look up 61461 on the word list, you'll find the word tori. And then you'll have to repeat that for as many words as you want on your password.
Some people might be worried that the dictionary of possible words is publicly available, but it doesn't matter. Think about it: the attacker also knows the valid characters in your keyboard when you create a regular password. What's difficult to guess is the order in which they go. The Diceware method swaps the 95 possibilities of a keyboard for 7,776 possibilities (i.e., the words).
Representing that in bits, we have that 7 , 776 = 2 ^ 12.92 , or that each word has around 12.92 bits of entropy. If you choose five words, that's 7 , 776 ^ 5 possibilities or 12.92 * 5 = 64.5 bits of entropy. A six-word password has about 78 bits of entropy and a seven-word one about 90 bits.
The beauty of Diceware is that you are converting real randomness into a passphrase; you know exactly how strong it is. This method essentially turns a dictionary attack into a much more computationally-intensive brute force one.
A passphrase generated through this method avoids many of the pitfalls we talked about before: you can choose just how strong you want it to be by adding or removing words, it's easy to type on your phone, and for most people, it's easier to remember than a random string.
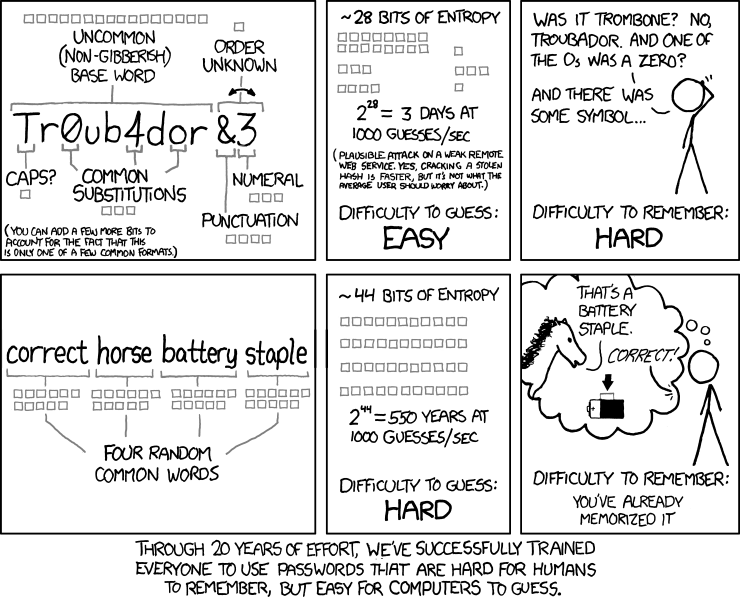
That's too short to be a good passphrase. Credit: xkcd.
And you don't need to buy dice if you don't have any lying around. You can use a random numeric generator for this, and it's sufficiently secure for most people.
The physical dice only certifies that your password wasn't tampered with (for example, if your computer was compromised when you created your password) and that nobody spied over your shoulder.
Other Word Lists
There are word lists available in other languages available on the official website. They aren't any less or more secure, just in a different language. You should use the language you're more comfortable with, as those will be easier to type and remember.
There are alternative English word lists with a few different attributes as well. The most well-known of those is perhaps the EFF list: it uses more common words, but they are longer on average.
It comes down to personal preference. You should check the official EFF article to compare both lists.
Driving home the point on security theater: mixing additional dictionaries doesn't make your passphrase more secure. If you mix three dictionaries, that will give an additional 1.5 bit of entropy per word... at that point; it's better to just use a single dictionary and tack an additional word at the end.
Diceware vs. Random Strings
While you can choose either method, as both are equally secure, it may make more sense to use one over the other depending on the situation.
For example, some websites limit the password length you can use – iCloud limits passwords to 32 characters.
This makes it impossible to create a Diceware password with satisfactory entropy – you'd be better off using a random string even if you prefer Diceware passphrases.
On the other hand, if it's a password, you can see yourself having to share with other people (e.g., the WiFi password), then telling them a list of words is way easier than spelling a 20-character string out loud.
The same goes for situations where you can't use the auto-fill feature of your password manager and are forced to copy the password by hand: much better to have a list of words.
So, How Strong Should Your Password Be?
Regardless of which method you prefer, you should consider using a password manager to generate and store different passwords for the different services and websites you use.
You choose which one you choose is up to you since different applications will appeal to different folks: for example, some people don't like storing their passwords on the cloud, while others enjoy the convenience.
(Keep in mind that not all password managers have passphrase generators, though, so that's something you'll have to look for when choosing one if you haven't already. KeePassXC has a Diceware generator that you can use alongside your cloud-capable password manager if it can't generate Diceware passphrases and you wish a convenient way to create them without dice.)
What's important is that your password manager will store all of your passwords for you, so it doesn't cost you anything to have 128-bit passwords for every website on your vault (length limits permitting)... so you can go ahead and 128-bit passwords for those.
And what about your master password? Well, it'll depend on your threat model and how well you are able to balance the things we talked about in this article.
Here are some entropy targets for your master password and situations where you can't use a password manager: 90+ bits (seven Diceware words) is secure, and probably the minimum you should strive for; 100 bits (eight words) is really secure, and 128 bits (ten words) will probably be secure until (or if) quantum computing becomes a thing.
Source: https://auth0.com/blog/creating-great-passwords/
0 Response to "Easy Passowrds to Type in With One Hand"
Postar um comentário